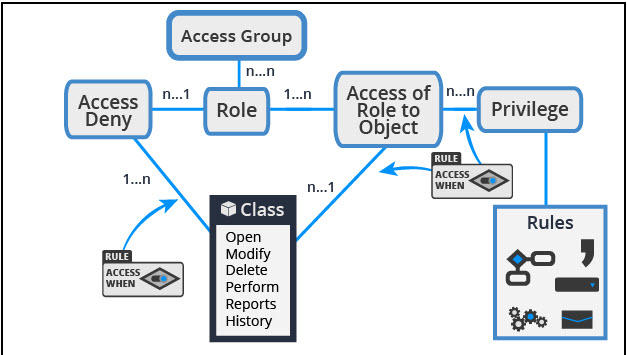
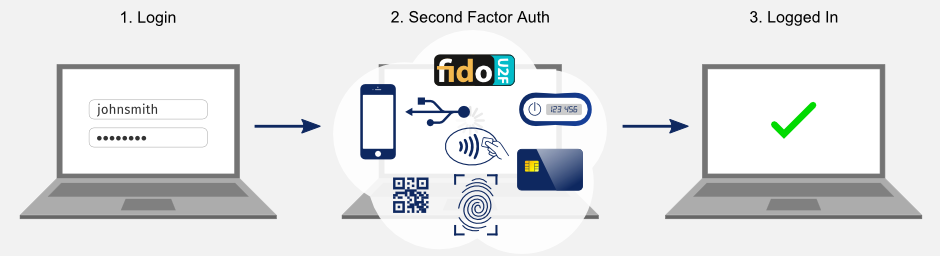
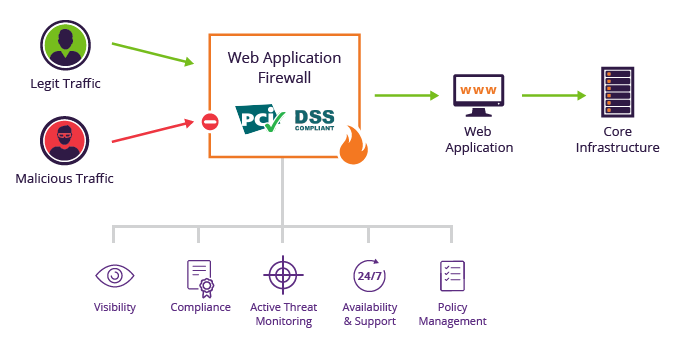
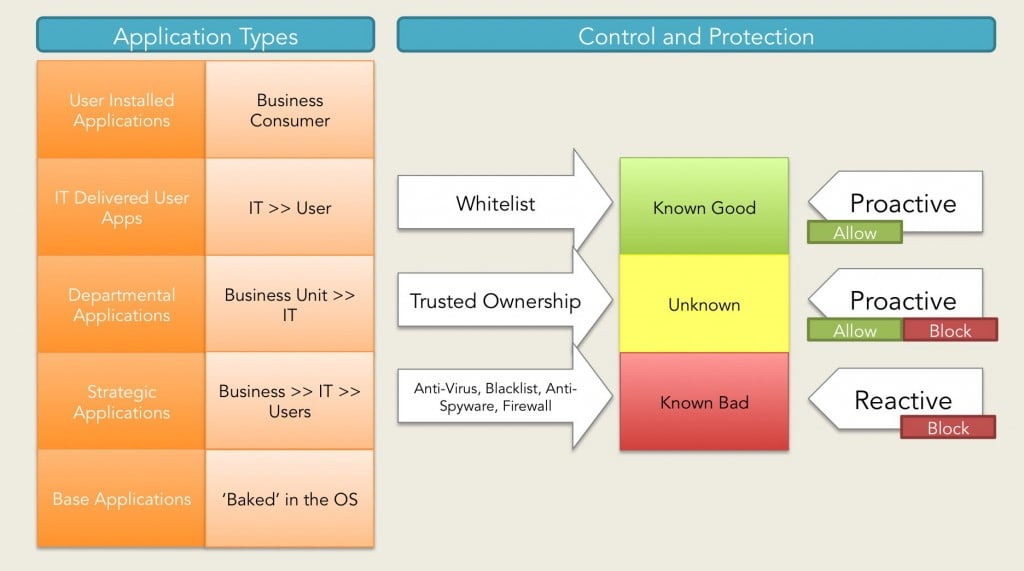
ISO 27001 Annex : A.9.4 System and Application Access Control | Infosavvy Security and IT Management Training
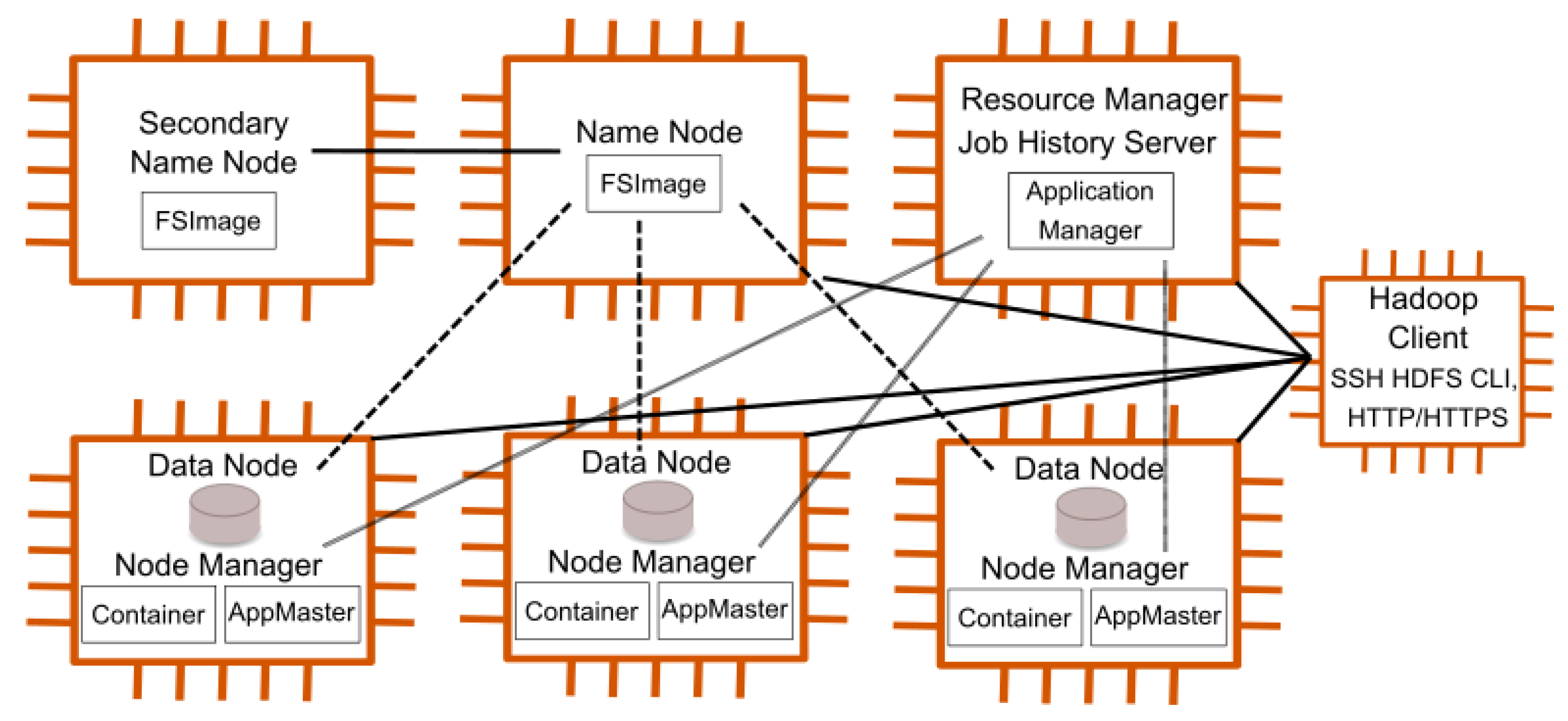
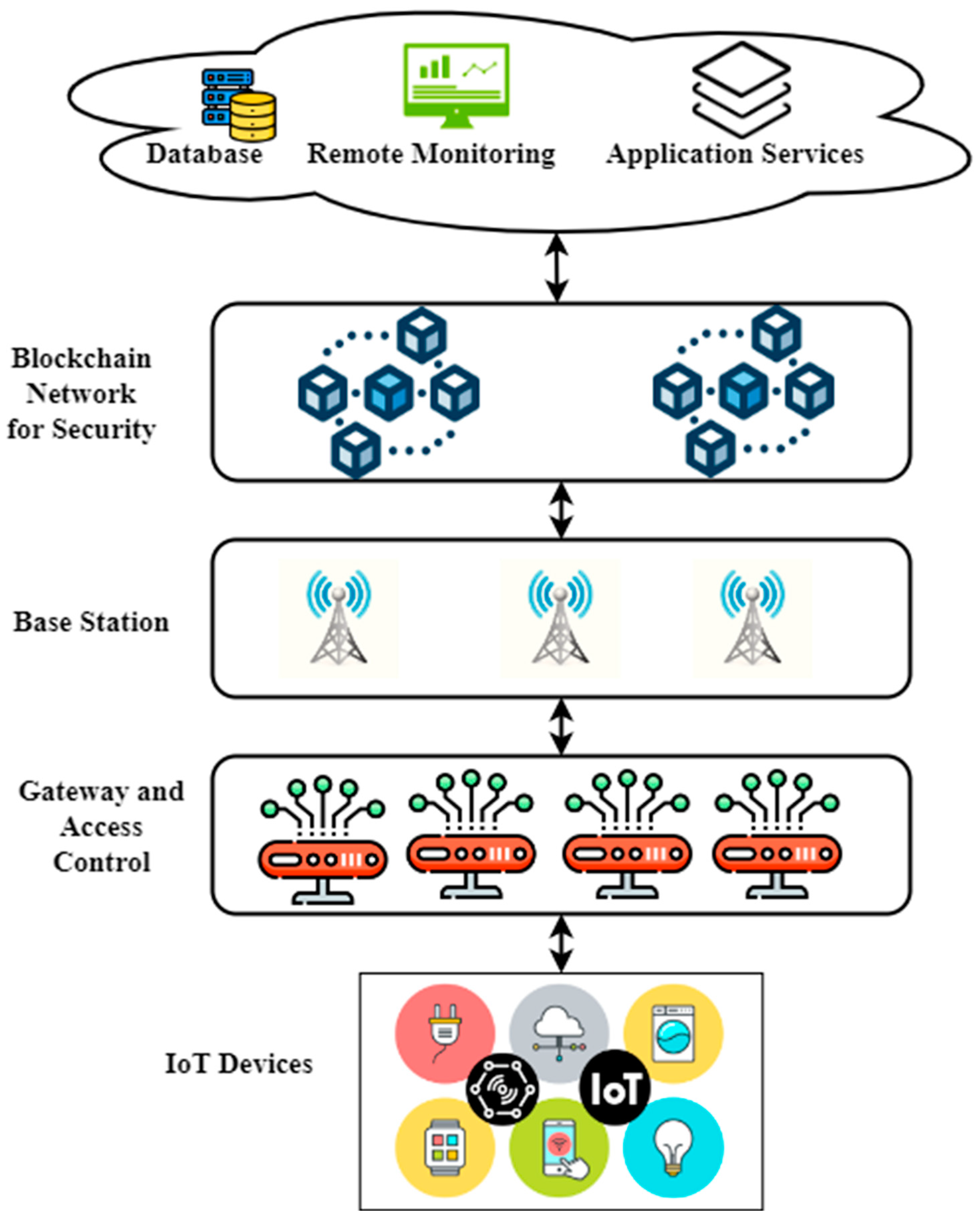
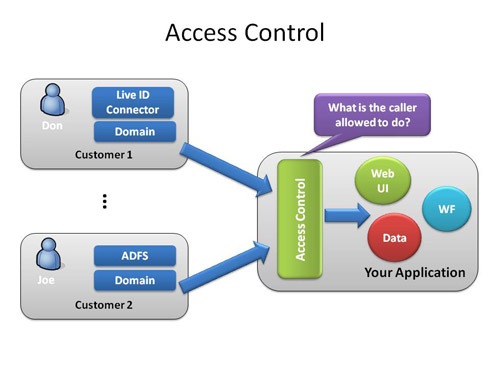
Applied Sciences | Free Full-Text | A Framework for Attribute-Based Access Control in Processing Big Data with Multiple Sensitivities

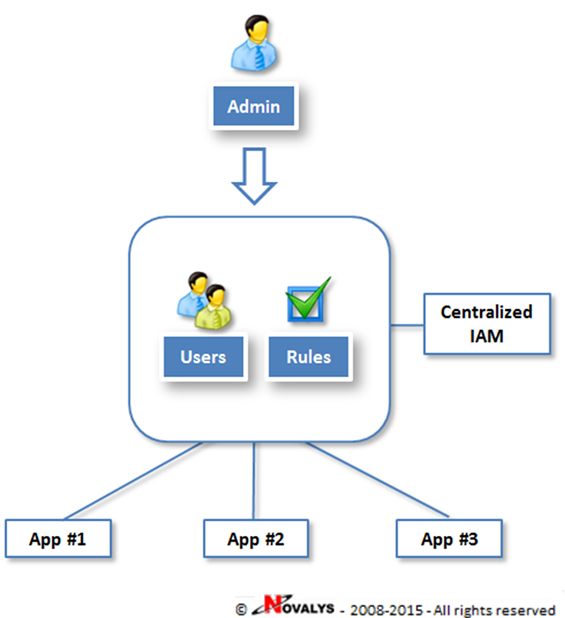
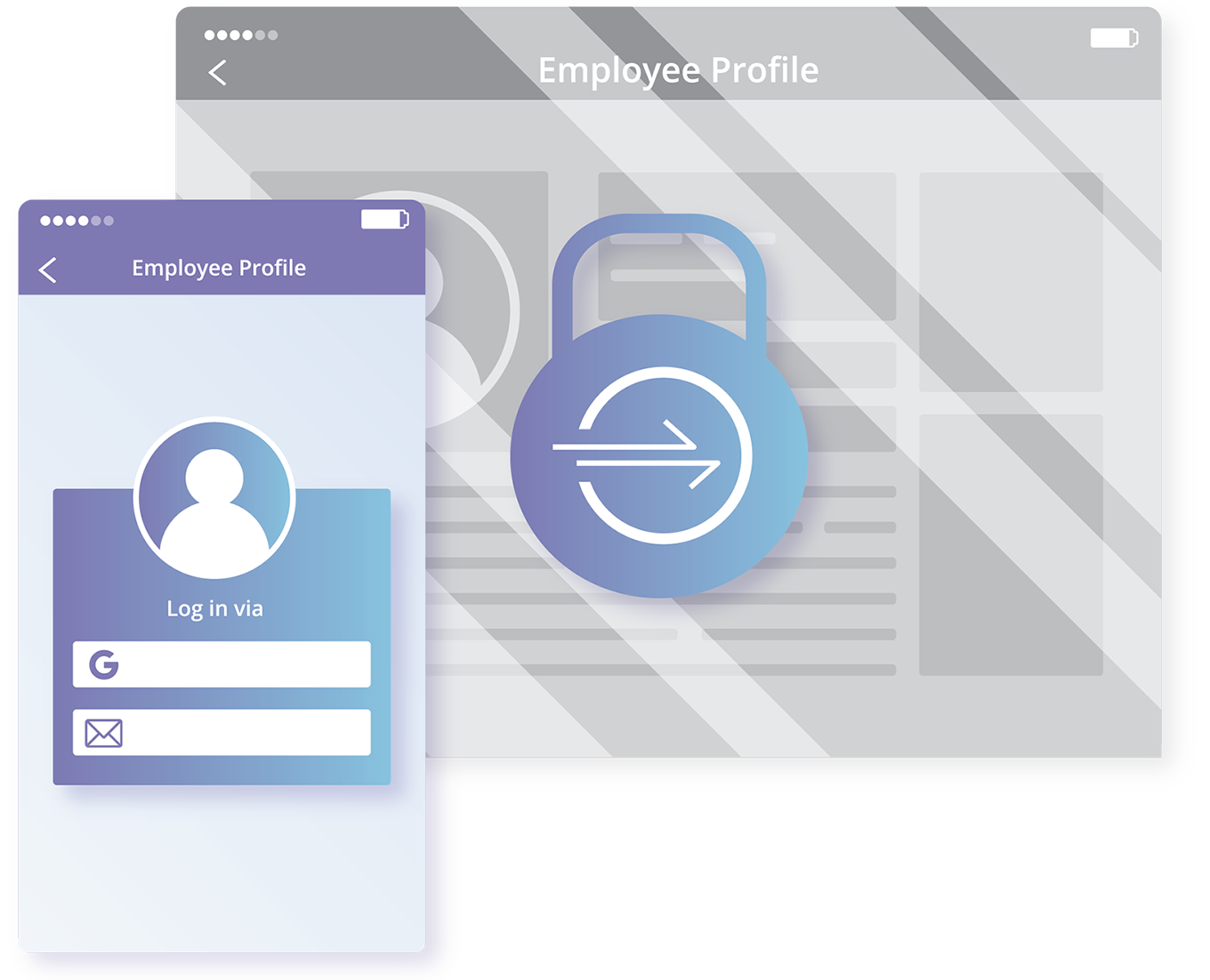
How to design access control system for Saas application | by Anna Savytska | Muzli - Design Inspiration